-
Posts
37,924 -
Joined
-
Last visited
-
Days Won
1,504
Everything posted by Marcos
-

[Win 10 & 8.1] What causes this border/shadow glitch?
Marcos replied to Dr. Blythe's topic in ESET NOD32 Antivirus
I don't see any issue in the screen shot. -
I don't know what the response from LiveGrid servers was, however, regardless of the response the cached file would have been either deleted or submitted. If it was deleted and nothing was logged, it had to be rejected by LiveGrid servers. Next time you can make a backup copy of such file so that we can investigate it further.
-
You don't have to care what action was exactly performed, otherwise you'd have to distinguish between clean files infected with a parasitic virus and other kind of threats that contains only malicious code. The point is that cleaning means removing the malicious code, ie. either the whole file or the malicious code added to otherwise legitimate files and also removing all references to the malicious file from the registry. A copy of the original file is always put into quarantine so that it could be restored later, if needed.
-
Cleaning means: 1, placing a copy of the original file to quarantine 2, deleting the whole malicious file or cleaning the malicious code in case of VBA macro malware or sanitizing the file in case of file infectors (viruses) 3, removing references to the malicious file from the registry as well as fixing possibly malicious modifications in the registry.
-

schedule weekly scan with shutdown
Marcos replied to andy_s's topic in ESET PROTECT On-prem (Remote Management)
This is not currently possible but we'll consider adding this option in the future versions of ESET security products. -
It's highly unlikely they would be false positives. Please post the appropriate records from the Detected threats log.
-

Detected Port Scanning Attack - Sonicwall
Marcos replied to Judg3man's topic in ESET PROTECT On-prem (Remote Management)
Please post a screen shot of the IDS exclusion that you have created as well as a screen shot of the firewall log with details about the detection. -
To my best knowledge, there are currently no plans to localize ESET SysRescue. It's an auxiliary tool intended for advanced users so the knowledge of English is assumed. Maybe this will change in the future with all-in-one language version of ESET Antivirus for Linux Desktop.
-
With ESET installed on all machines with access to the NAS, protection should be ensured. If a NAS is equipped with an x86 compatible CPU and running Linux, it should be possible to install ESET File Security for Linux on it as well.
-
The blocked address is likely related to CoinMiner. If you are still getting the notification about blocked access to the url, email samples[at]eset.com and enclose the archive generated by ELC (or a download link to it) as well as a description of the problem.
-

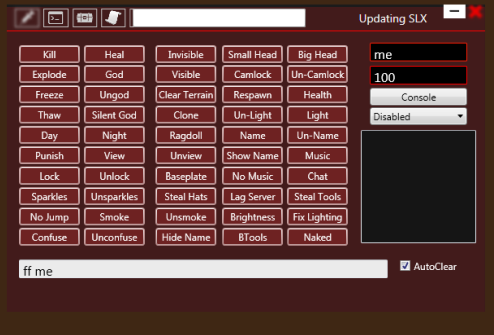
ESET not detect trojan QTXWPF.exe
Marcos replied to Descloix's topic in Malware Finding and Cleaning
Correct. Sometimes even > 40 AVs in VT report even perfectly benign files as malware. That is also the reason why VirustTotal has the following listed among best practices: The data generated by VirusTotal should not be used automatically as the unique means to blacklist/produce signatures for files. i.e. Antivirus vendors should not copy the signatures generated by other vendors without any other scrutinizing on their side. Almost all AVs detect the file with generic detection names so they are not detections based on manual analysis of the file by researchers and therefore are not accurate. By the way, here is how the game hack tool looks like when run: -

ESET not detect trojan QTXWPF.exe
Marcos replied to Descloix's topic in Malware Finding and Cleaning
We are not going to detect a file as malware based on what a user says if it's not malicious. Detection is always added based on thorough analysis of the code. The OP was also referring to a dll which is benign and is included with many legitimate software. -

ESET not detect trojan QTXWPF.exe
Marcos replied to Descloix's topic in Malware Finding and Cleaning
This is a very generic name for a detection and may cover virtually anything. By the way, SciLexer.dll is included with a lot of legitimate and benign software. -

ESET not detect trojan QTXWPF.exe
Marcos replied to Descloix's topic in Malware Finding and Cleaning
Did you debug the file and analyze its code that you are saying it's a dangerous trojan? Based on what did you make the assumption that it's dangerous? -
Please report possible false positives as per the instructions at https://support.eset.com/kb141/.
-

ESET not detect trojan QTXWPF.exe
Marcos replied to Descloix's topic in Malware Finding and Cleaning
Not malware but a game tool. We'll add detection as a potentially unsafe application. The application doesn't pose any security risk.