-
Posts
196 -
Joined
-
Last visited
-
Days Won
7
Posts posted by BALTAGY
-
-
I personally never use sleep, i only use screen lock, and problem still there
-
Same here with Firefox, not sure if it's related to Firefox


-
5 hours ago, itman said:
Appears the recovery procedure is create a real-time exclusion for the note detection and then remove the note from quarantine to be able to view the note. A bit of a stretch for the average user.
That's what i'm talking about, also many users won't even know it's a ransomware and could be waiting online for sometime then the ransom will keep downloading other viruses etc until the system freeze and you can't open it and for sure the ransom note also will be gone and you can't use it if the Decryptor require it
This scenario can easily happen, if the anti-ransomware need to read the ransom note to be triggered then it also can read it and leave it -
4 minutes ago, Marcos said:
For forensic analysis for instace when trying to find out how encryption occurred.
how encryption occurred is not in ransom note, ransom note only contain info how to pay and emails and the important part is the id
Even if anyone removed the ransomware it self from the system and didn't delete the ransom note it won't do anything but it will help the user to determine the ransom name and version by uploading it to some sites like id ransomware
I hope you consider leaving the note as it contain an important info and if something wrong happen to the system the user may not be able to recover the files without it like GandCrab it's ransom note is important to recover the files -
Just now, Marcos said:
It must be detected. Unfortunately, that also means that an action has to be selected. The user can exclude a particular file from derection in order to be able to read the notes.
Why it must be detected if it harmless ? i'm just curios
-
Just now, Marcos said:
The user is asked for an action upon detection. While the best would be to detect and log the detection with no cleaning or promting at all, such behavior is not supported. Adding detection without cleaning just for the sake of ransomware notes would be quite expensive in terms of resources.
Not sure i get what you mean ? Yes the user is asked but if you choose ignore it will keep come up many times until you exclude it or delete it
I just want to know what the point of delete the ransom note ? it's harmless also if ESET can't detect the ransomware it self and only delete the ransom note after sometime while ransom is running and downloading other viruses etc, the user may not be able to recover the note from quarantine -
10 minutes ago, Marcos said:
Any file that is cleaned is also quarantined so that users can restore it if necessary. Moreover, ransomware notes are not cleaned automatically in default cleaning mode.
You mean this option ?
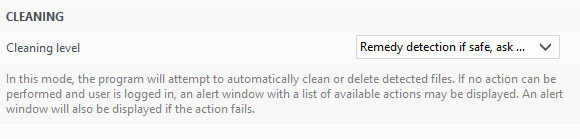
Also i know it can be restored but i must disable the protection to restore it
What the point of deleting it ?
Here's an example, it's being deleted via database, and here's virus total
https://www.virustotal.com/gui/file/c65b7b3734f8f42687487c69c50da5ba31915d092ae8bca3ae4d1670300f652c/detection -
Hi,
Why ESET is deleting Ransomware notes ? it contain important info like ID that can be used to decrypt the encrypted files !
Thanks -
5 hours ago, itman said:
Yikes! This is still coming up after three years.
I wrote about this here: https://forum.eset.com/topic/10792-ransomware-simulators-a-detailed-analysis/ and methods employed by Ransim and why Eset ignores their tests.
I remember i did read something about it but did search and didn't find anything, thanks for the info
-
4 minutes ago, Marcos said:
Simulation tests do not tell anything about how a particular AV would perform in a real world with actual malware. We don't react to it rather deliberately.
Isn't these testes act like a real ransomware ? why ESET don't block the operation of encrypting these files ?
-
Hi,
I came across this tool that should be testing some ransomware scenarios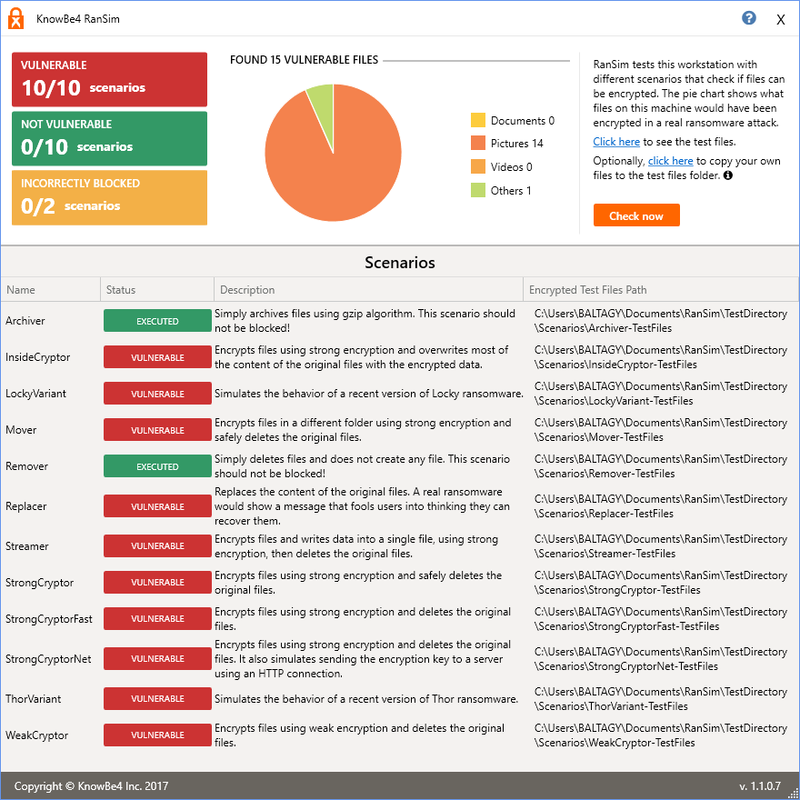
Original link
https://www.comss.ru/page.php?id=3594
Shouldn't be ESET block these testes ? -
I was just testing the custom scan now and selected "Operating memory,Boot sector, WMI, System registry, Desktop"
I see some files being scanned too many times like storage.dll in SysWOW64
And some files took ESET sometime to finish ( i can send one of them if you like )
Scan finished after 25min
Did a custom scan again for the C drive ( System Drive ) with Boot sectors and UEFI selected by defaults and scan finished after 5min only -
Hi,
Why Advanced heuristics/DNA signatures option is not enabled by defaults ? dose enabling this option will slow down the system ?
Thanks -
18 minutes ago, local said:
can you give me one-two examples when ESET acknowledged an issue and did not blame the customer???
2 hours ago
You have 38 posts of complains, if ESET is so bad and there's a free other products are better with 100% protection as you said before, let me ask you again since you ignored to answer every time
Why you still using ESET if you see it very bad ?
Are you even using ESET ? -
Just now, itman said:
Then something is wrong with how FireFox is configured. In the latest version of Firefox, it uses the Window root CA certificate store by default. In other words, Eset's root certificate is no longer required to be installed in FireFox's Authorities certificate store.
I did test v13.0 and v12 all of them have same problem in a clean system only ESET and Firefox
But once i installed chrome it works fine
I think ESET need to check it, maybe a module update is needed -
Here's the logs after downloading eicarcom2.zip and while ESET didn't add it self into Firefox
It's a clean system only ESET + Firefox + IDM installedeis_logs.zip
Update:
Just installed chrome in this clean system and everything works fine
Update2:
wilderssecurity.com/ shows Adguard certificate in chrome but ESET still block eicarcom2.zip -
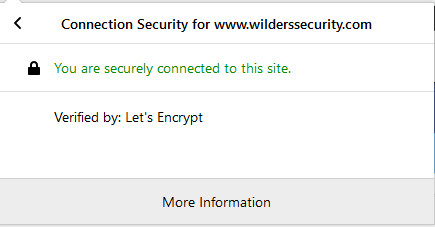
Did test in a clean system without Adguard and ESET don't show in Firefox -
Just now, itman said:
Also if Eset is performing SSL/TLS protocol scanning, any like feature in Adguard should be disabled. Same principal appears here as to use of two real-time scanners together.
Adguard only block Ads, but since the last v7.4 i see "Your browser is being managed by your organization." in Firefox settings and Adguard certificate is in all sites
I'm testing only ESET+IDM+Firefox in a clean system and will collect the logs -
3 minutes ago, itman said:
Does the Eset root cert. show on this web site: https://www.wilderssecurity.com/ ? If Adguard's shows, there's a problem.
It's Adguard
-
12 minutes ago, itman said:
The only reference I see in IDM relating to AV use is shown below. What does it show on your system?
Also note that eicar.com and eicar.com.txt are blocked by ESET but not eicar_com.zip or eicarcom2.zip
Another note that i'm using Adguard and i see Adguard certificate in all sites including forum.eset.com -
2 minutes ago, itman said:
The only reference I see IDM relating to AV use is shown below. What does it show on your system?
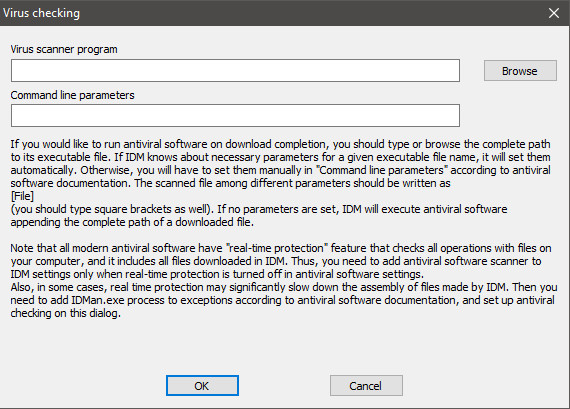
It's empty, also i never needed to add anything to it since ESET did block before IDM can capture the link -
-
11 minutes ago, itman said:
Are you using the stand-alone installed version or the FireFox add-on?
If you install IDM, it will install the Firefox add-on, same happen with all browsers
Also i have the file Marcos asking about -
4 minutes ago, Marcos said:
Is eicar detected upon download with SSL filtering enabled? https://secure.eicar.org/eicarcom2.zip
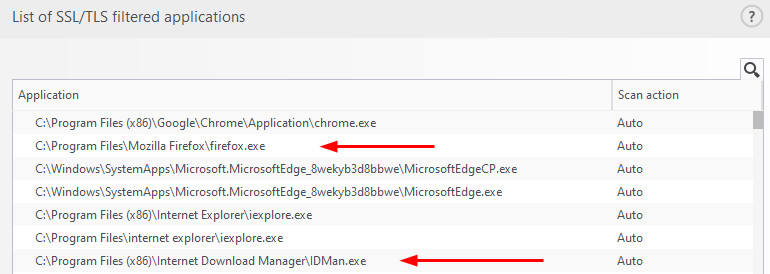
It don't get detected while downloading using Firefox but it get blocked on Chrome
Update:
I'm using "Internet Download Manager" and it got detected after i stopped IDM and used Firefox instead
But in Chrome it get blocked before IDM can catch the link





Firefox browser problem when using eset
in ESET Internet Security & ESET Smart Security Premium
Posted
Same here, when you search for "ocean of games" for example then left click on search results on Firefox, nothing happen, and no message from ESET
On Chrome it open the site on new tab with ESET alert