-
Posts
36,133 -
Joined
-
Last visited
-
Days Won
1,439
Posts posted by Marcos
-
-
I don't know what the response from LiveGrid servers was, however, regardless of the response the cached file would have been either deleted or submitted. If it was deleted and nothing was logged, it had to be rejected by LiveGrid servers. Next time you can make a backup copy of such file so that we can investigate it further.
-
How do you know that gamer mode doesn't activate automatically? Did you schedule a scan to be run at a time when an application was running in full-screen mode and the scan was actually started?
-
6 hours ago, WhiskeyRiver said:
I suspect the eset programmers solved it once they confirmed that turning HIPS off cured it.
So one of the laptops got extensive scrutiny and was finally solved by putting it the pre-release eset update channel after the programmers had their way with it.
We didn't change anything with regard to the issue and are currently anticipating more information / resolution from Microsoft.
-
You don't have to care what action was exactly performed, otherwise you'd have to distinguish between clean files infected with a parasitic virus and other kind of threats that contains only malicious code.
The point is that cleaning means removing the malicious code, ie. either the whole file or the malicious code added to otherwise legitimate files and also removing all references to the malicious file from the registry. A copy of the original file is always put into quarantine so that it could be restored later, if needed.
-
Cleaning means:
1, placing a copy of the original file to quarantine
2, deleting the whole malicious file or cleaning the malicious code in case of VBA macro malware or sanitizing the file in case of file infectors (viruses)
3, removing references to the malicious file from the registry as well as fixing possibly malicious modifications in the registry. -
There should be only shortcuts (.lnk files) in these folders. If you scan the folder with the on-demand scanner, does it take long or the scanner freezes?
-
This is not currently possible but we'll consider adding this option in the future versions of ESET security products.
-
If you think that ESET is responsible for the crashes, please contact customer care and provide a complete memory dump from such crash for perusal. Also supply logs gathered by ESET Log Collector.
-
How do you know they were actually submitted? If someone else has submitted them, then the submission was rejected and the files in the cache were deleted.
-
Please generate a dump of ekrn.exe via the advanced setup -> tools -> diagnostics -> create (dump) when you notice a high memory use by ekrn. Then gather logs with ESET Log Collector and provide us with the generated archive for analysis.
-
It's highly unlikely they would be false positives. Please post the appropriate records from the Detected threats log.
-
1 hour ago, Leigh Glaus said:
All my issues were on x86, but I haven't tested x64 as all our network workstations have to run 32-bit. @Marcosworkaround by disabling HIPS Protected Service seems to be working fine in the interim.
If you re-enable protected service, does the issue occur within the next few hours?
-
You can find the Protected service setting in the HIPS setup.
-
10 minutes ago, Dick said:
I have exactly the same issue.
The problems started after upgrade to 1803 on May 5 2018.
It has been restarted several times since then.
Below is a summary of the ESET events since the "Feature update to Windows 10, version 1803" was installed.
No such errors prior to that date..
As this has been reported several times during the past weeks I wonder what the solution is (if any).Microsoft is already analyzing the issue. Does temporarily disabling protected service and rebooting the machine make a difference or the issue returns after a while?
-
Please post a screen shot of the IDS exclusion that you have created as well as a screen shot of the firewall log with details about the detection.
-
To my best knowledge, there are currently no plans to localize ESET SysRescue. It's an auxiliary tool intended for advanced users so the knowledge of English is assumed. Maybe this will change in the future with all-in-one language version of ESET Antivirus for Linux Desktop.
-
With ESET installed on all machines with access to the NAS, protection should be ensured. If a NAS is equipped with an x86 compatible CPU and running Linux, it should be possible to install ESET File Security for Linux on it as well.
-
The blocked address is likely related to CoinMiner. If you are still getting the notification about blocked access to the url, email samples[at]eset.com and enclose the archive generated by ELC (or a download link to it) as well as a description of the problem.
-
9 minutes ago, claudiu said:
OK then, that means 23 from 66 antiviruses on Virus Total must be stupid to classify this as "Trojan" when in fact doesn't pose any security risk.
Correct. Sometimes even > 40 AVs in VT report even perfectly benign files as malware. That is also the reason why VirustTotal has the following listed among best practices:
The data generated by VirusTotal should not be used automatically as the unique means to blacklist/produce signatures for files. i.e. Antivirus vendors should not copy the signatures generated by other vendors without any other scrutinizing on their side.
Almost all AVs detect the file with generic detection names so they are not detections based on manual analysis of the file by researchers and therefore are not accurate.
By the way, here is how the game hack tool looks like when run:
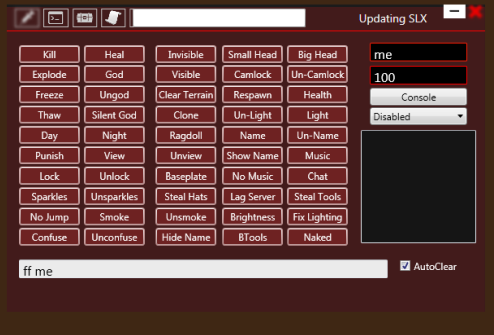
-
We are not going to detect a file as malware based on what a user says if it's not malicious. Detection is always added based on thorough analysis of the code.
The OP was also referring to a dll which is benign and is included with many legitimate software.
-
Quote
This is W32.Trojan.Gen the least.
This is a very generic name for a detection and may cover virtually anything. By the way, SciLexer.dll is included with a lot of legitimate and benign software.
-
1 minute ago, claudiu said:
I do not understand how ESET classifies this as "unsafe application" which doesn't pose any security risk......
Did you debug the file and analyze its code that you are saying it's a dangerous trojan? Based on what did you make the assumption that it's dangerous?
-
Please report possible false positives as per the instructions at https://support.eset.com/kb141/.
-
Not malware but a game tool. We'll add detection as a potentially unsafe application. The application doesn't pose any security risk.




[Win 10 & 8.1] What causes this border/shadow glitch?
in ESET NOD32 Antivirus
Posted
I don't see any issue in the screen shot.